Malware is a term used to describe unwanted software that is used to gather information, gain access to private systems, display unwanted advertising, or disrupt normal system operations. It is defined by its malicious intent and runs against the user’s permission. It is an umbrella term used to describe a variety of intrusive software, including viruses, worms, Trojan horses, ransomware, and macro viruses. Let’s take a look at each.
What is a Virus?
A virus is a malware program that when executed, replicates by inserting copies of itself to infect other programs, data files, or the boot sector of the hard drive. They perform some type of harmful activity, such as utilizing computer resources, like hard disk space, CPU, and ram. Viruses can also access private information, corrupt data, or log keystrokes. They can even make the computer completely unusable. However, not all viruses are of a destructive nature. Some are programmed to send advertising pop ups to your screen.

Where do Viruses come from?
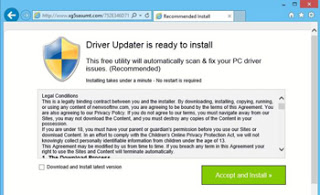
What are symptoms of a virus infection?
The most common symptoms of a virus infection are the computer not booting or being greeted by a “blue screen” at startup, slow performance, missing files, pop-up ads, slow internet connection, or random crashing.
What are Worms?
Worms are a special kind of virus, in that they do not need a host program to run. Worms take advantage of the network infrastructure to spread themselves. These can wreak havoc because it can send out many copies of itself from one infected system. For example, a worm can send a copy of itself to everyone listed in an address book, then those newly infected systems continue to spread to others, and so on. Due to the nature of a worm, they consume much network bandwidth, causing servers to crash or bring network traffic to a halt. They can also install a backdoor for the purpose of allowing unauthorized access.

Where do Worms come from?
Worms can come from an email attachment or a downloaded file. They can also come from peer-to-peer file sharing networks, such as the bit torrent, or clicking on links to untrusted or unfamiliar websites.
What are symptoms of a Worm?
Common symptoms of a Worm are similar to those of a virus, slow performance, crashing, system errors, and “blue screens”. Emails being sent to contacts without the user’s knowledge or programs opening and running automatically are also common.
What is a Trojan Horse?
Trojan horses, commonly referred to as “Trojans” are a type of virus that is disguised as a program that may appear interesting or useful in order to get the user to install it. Unlike other viruses, Trojans generally do not attempt to infect files nor replicate themselves. Trojans can cause mild to severe damage, depending on its intended purpose. On the mild side, they can change the desktop icons, change the homepage, or add toolbars or extensions to the web browser. The primary purpose of a Trojan horse is to open a backdoor in the system to allow unauthorized access. With this backdoor open, a number of other viruses can enter the system, such that can cause data theft or loss, data corruption, or install ransomware. It can give an unauthorized user access to the infected system like controlling an attached webcam, watching a user’s screen, or even take control the system remotely. Trojans can also install programs to make the computer act as a proxy for illegal activities or attacks on other computers.
Where do Trojans come from?
Trojans are spread with the help of Worms. As worms travel the internet, they can install a Trojan in any computer they meet. They can come from an email attachment disguised as a common file type. For example, a file with the name “picture.jpg.exe” may appear to be a picture file, but the user may only see the “picture.jpg” and not notice the “.exe” and therefore assumes that it is a safe picture file and when opened, the virus installs itself.
What are the symptoms of a Trojan Horse?
Symptoms can include data loss, data corruption, random computer crashes, or a misdirected home page. No apparent symptoms can be seen at first, such as the case with some ransomware, then they can manifest themselves at any time.
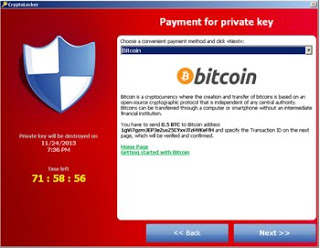
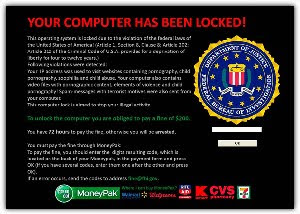
What is Ransomware?
Ransomware is malware that when installed, shows up on the screen, looks authentic, and appears to do a scan of the system. These scans are not real and the items they find are false positives, designed to scare the user to purchase the “full version” of the program. The primary purpose is to try and extort money from the user. Ransomware can actually run silently in the background, either encrypting data on any drives or network shares, or opening network ports to allow access to an unauthorized user.
Where does Ransomware come from?
Ransomware can come from clicking an internet link, or opening an attachment in an email disguised to be unsuspicious. “Drive-by downloads” happen when clicking on a disguised pop-up window or visiting an unknown website. Ransomware is becoming much more prevalent and we’ll take a closer look at Ransomware in a subsequent blog post.
What is a Macro Virus?
A macro virus is a malicious program that infects Microsoft Office applications, such as Word and Excel. These are also called “document” viruses. Office applications allow the use of programming scripts, or macros, to be embedded in the document. These scripts are coded instructions that can automate tasks within the document. When the file is opened, the script is executed, and begins to infect other Office documents.
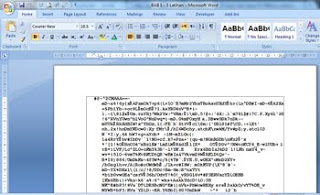
What are the symptoms of a macro virus?
Symptoms of a macro virus can include only the ability to save the document as a template, rather than a document, the “macro” and “customize” commands no longer appear in the “tools” menu, or unusual or unexpected messages appear when a document is opened.
Where do Macro viruses come from?
Macro viruses can come from email attachments, external media, and the internet. Since macro viruses depend on the application rather than the operating system, they can infect any computer running Microsoft Office, including Apple Macs.
How to protect against Malware?
Making sure the operating system has the latest updates and having an updated antivirus program can reduce the chances of infection greatly, but the best defense is being aware. Using strong passwords and keeping critical data backed up is always best practice. Notice what is being clicked on while online and the complete filename of downloaded files or email attachments.
At Skyline IT Services, we present our managed clients with solutions, management, data protection, and consulting. We provide the latest antivirus protection, set strong password policies, and use industry standard firewalls. This allows our clients to spend more time focusing on growing their business and less time worrying about their IT needs. Our managed antivirus program informs us when a desktop or server has been infected. In most cases, we are able to remotely remove the infection without any disruption to the user. Our SkyVault™ backup appliance keeps a backup of all critical data and can seamlessly restore missing or corrupt data.



